Directory Services
A Waterloo Polaris Technical Description Draft
Introduction
Every significant computing installation eventually requires some way to store and retrieve common information ranging from phone numbers to mundane operational values like printer driver settings. Usually, ad hoc approaches are employed (simple lists), but eventually they are replaced with general-purpose directory services built upon proper databases and with distributed and fault-tolerant technologies.
This paper discusses how Waterloo Polaris will migrate to new open protocol directory services as part of our Phase II strategy.
Several points discussed here may change or are open for discussion. We will likely proceed with an initial implementation and refine it based on experience and product availability as we migrate more information to this directory service.
The Present
To date, Waterloo Polaris has relied on Watstarís primitive directory services to answer all sorts of questions such as:
Each of these is answered by a database lookup of (a) a specified parameter (e.g. login restrictions) and (b) one of the following pieces of information:
|
Key |
Description |
Examples |
|
local station |
information peculiar to workstation |
|
|
station groupings |
stations are often grouped into similar collections. eg. a classroom of nearly-identical machines, or common characteristics in a group of offices |
|
|
user account |
characteristics special to this user |
|
|
user server |
characteristics shared among all users of a particular home server |
|
|
global information |
information of the network
|
|
Much of the information is naturally decentralized. Faculties and departments have authority to effect all sorts of changes, so obviously they need the ability to update the information in the directory.
The following graph demonstrates decentralized directory services in place today. The example given is a Math user named erick@cygnus1 who logs into the Engineering Helix computer lab located in EL-108.
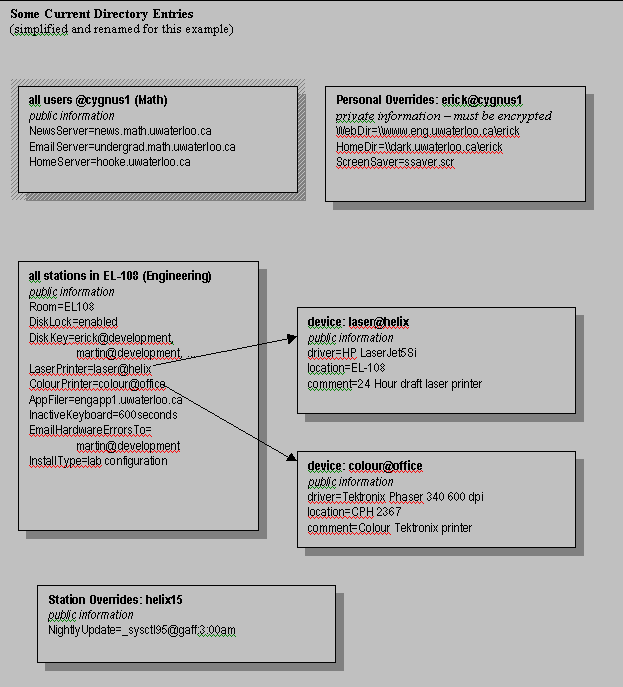
The Helix manager has listed laser@development and colour@office as the closest laser printers. Unless there are reasons to avoid using them, Waterloo Polaris automatically uses the directory services to fully configure the current session for these printers.
Other values are chosen by the userís home faculty/server. For example, the Homeserver hooke is listed. Waterloo Polaris automatically connects this user to the appropriate home directory of this Network Applicance. The device could just as easily have been an NT server or a Unix server.
Some choices are perhaps less obvious. IST has organized a news server hierarchy based on faculty, and so all Math students are expected to read their news from news.math.uwaterloo.ca whether the userís computer is in Math or not. Waterloo Polaris directory services honour and actually implement that strategy.
What is notable is that our directory services are system-wide yet have distributed control. A Math student using an Engineering computer gets a reasonable set of values based on decisions appropriately made by either Math and Engineering. If the user wishes to redirect to a printer in Arts, then Arts-specific information also enters the picture. Even non-polarized servers (such as Graphic Services, Watserv1, etc.) are easily accessible by our users as soon as we include appropriate entries in our directory.
The current system is easily extensible, and so it has become pervasive in almost every aspect of Waterloo Polaris. Its successor will need to be fast, reliable and offer additional benefits.
The major problems are:
And so we plan to evolve to the next logical step.
The Future
The world is increasingly turning to open standards to fulfil such directory service requirements.
The classic directory services example in open protocols is X.500, a component from OSI world. X.500 encompasses both the overall namespace (ie. how you describe data) and the protocol for querying and updating it (known as DAP or Directory Access Protocol). DAP would be great, except that it is overly complex, with several components that are best described as esoteric. This complexity results in a large memory footprint and so X.500 would be unacceptable for workstation parameter settings.
As usual, the Internet community preferred a smaller and simpler directory service strategy. The best parts of X.500 are retained, but the protocol and schema were adapted for the TCP/IP world. The resulting system is LDAP, or "Lightweight Directory Access Protocol".
LDAP is quite a hot topic. Itís quite useful, and client implementations are small enough that we can leave it resident in the computer to answer questions as they arise.
In the enterprise, LDAP is often integrated into PH, Whois and other services. On the desktop, Netscape Navigator, Internet Explorer, Microsoft Mail and many other programs are including LDAP query features. Novell Netware now supports LDAP access to its NDS (Netware Directory Services), Microsoft Exchange has LDAP serving capabilities.
Finally, Microsoft NT 5 promises to offer LDAP as one way to host its Active Directory services (that component is also available for NT 4 today).
Anyone planning client/server directory services for TCP/IP based networks should be considering LDAP as soon as possible.
While LDAP and X.500 define the transmission and representation of data, they do not specify the backend store of data. Often, LDAP is a lightweight front-end to a sophisticated X.500 service, or to other LDAP servers, or to a local database technology (dbm, Oracle, NDS, etc.).
LDAP can also provide secure access to private data using secure communications such as Kerberos or SSL (secure socket layer), but the latest LDAP specifications lack the details necessary to ensure security interoperability between vendors.
There are several shortcomings, such as the absense of an open standard data replication protocol between servers.
While LDAP is a standard, it is a weak standard because key components are either missing or incomplete. LDAP clients will usually be able to perform most primitive operations on most LDAP servers, but different implementations will have difficulty as soon as we try anything slightly more complex. LDAP is not as perfect as SMTP Email (and Emailís not perfect yet), so interoperability is a bit strained. In implementation terms, this really means we can theoretically work with anything, but must conduct tests with any particular product before assuming it is compatible with our other products.
The Plan
Waterloo Polaris needs to move directory services off of Watstar, and LDAP appears to be the best solution. The total solution, of course, is more than just the name of a protocol.
The basic plan is:
Basic Protocols and Products
Clients
All Waterloo Polaris client stations now have client drivers, and can talk LDAP v2 and v3 today as well as using the traditional directory services Ė a unified directory service to allow a comfortable migration.
In the coming months, some of our utilities will adapted to use the unified directory service. In time, the Watstar server component will become less relevant and eventually eliminated.
Also, SSL and other appropriate mechanisms will be added to supplement missing or limited components of LDAP.
Servers
Several LDAP server products exist for both NT and Unix environments. Examples of both have already appeared on campus, though each have some different aspects, particularly in regards to security, and some are easily tied to extensible databases while others are more simplistic.
Both NT and Unix LDAP servers can support userid/password authentication and authorization, and some can forward the authentication data to other authentication standard devices, including PDCs (Primary Domain Controllers) compatible with the campus ID-Auth project.
The LDAP strategy may reduce direct client interaction with the authentication server, but the authentication request will simply come from the LDAP server.
Administration Tools
Some workstation-level tools will use the Waterloo Polaris LDAP drivers which are simply Win32 level drivers (95, NT, etc). However, many campus operations have Unix or other needs.
For Unix and NT, several LDAP tools already exist.
Furthermore, it will often be reasonable for some programs to interact directly with the backend database using Perl, Oracle tools, or whatever is necessary or appropriate.
Big Issues
Performance
There will be a lot of client requests. Performance monitoring will be necessary on LDAP servers, just as on any other important servers.
Reliability
The directory services are an essential component of the system. Even logins become extremely difficult if directory services are down for any period of time. Furthermore, the system should be resilient enough to survive networking faults which temporarily isolate particular faculties, with the consequences being felt only by users who try to use resources on the other side of the networking fault.
In many cases, we will probably look at some faculty-located LDAP server, and a healthy bit of replication to improve fault tolerance. Also, the server should be backed up regularly, and the database stored on a disk which will not fill.
Consistency
Directory services are only useful if consistency is maintained. For example, the object names and uses must be consistent, mandatory fields must be set, and there must be adherence to certain protocols (like SSL) for compatibility.
It would also be appropriate that some cross-campus people have read/write access to the LDAP server databases to assist with the operations of each faculty constituency.
Ideally, we would use a campus LDAP configuration on faculty servers that would package these commonalties. However, secondary LDAP servers of any type could conceivably be integrated.
Distributed Management
There are several goals to our centralized/distributed plans:
Clearly the database management mechanisms need to be designed to deal with the hierarchical nature of some data. While much of the data may be housed on a faculty server, a small set of individuals will need read/write access to update parts of it.
For example, a printer in the Systems Design DASL lab would be controlled by Systems Design staff. If the printer was broken and routing moved to laser@gaff, the Systems Design staff would want to change the entry:
Likewise, the same staff will likely need the ability to add or purge large numbers of entries whenever convenient, often using ASCII lists.
There are several ways of accomplishing this, we just need to plan a consistent way right from the start, and hopefully use intelligent mechanisms which avoid many little LDAP servers across campus.
The LDAP directory services described for Waterloo Polaris could be integrated with other campus plans, or could simply co-exist with little integration. Such implementation issues will be resolved through interaction between the faculties, departments, IST, etc. as the implementation moves forward.
Draft Oct 8, 1998, Erick Engelke